Interface AdminMgr
-
- All Superinterfaces:
Manageable
- All Known Implementing Classes:
AdminMgrImpl,AdminMgrRestImpl
public interface AdminMgr extends Manageable
This class performs administrative functions to provision Fortress RBAC entities into the LDAP directory. These APIs map directly to similar named APIs specified by ANSI and NIST RBAC models. Many of the java doc function descriptions found below were taken directly from ANSI INCITS 359-2004. The RBAC Functional specification describes administrative operations for the creation and maintenance of RBAC element sets and relations; administrative review functions for performing administrative queries; and system functions for creating and managing RBAC attributes on user sessions and making access control decisions.
RBAC0 - Core
Many-to-many relationship between Users, Roles and Permissions. Selective role activation into sessions. API to add, update, delete identity data and perform identity and access control decisions during runtime operations.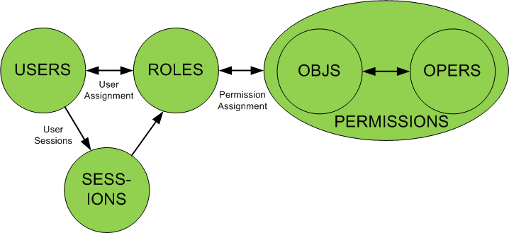
RBAC1 - General Hierarchical Roles
Simplifies role engineering tasks using inheritance of one or more parent roles.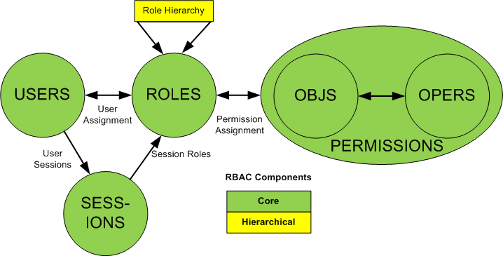
RBAC2 - Static Separation of Duty (SSD) Relations
Enforce mutual membership exclusions across role assignments. Facilitate dual control policies by restricting which roles may be assigned to users in combination. SSD provide added granularity for authorization limits which help enterprises meet strict compliance regulations.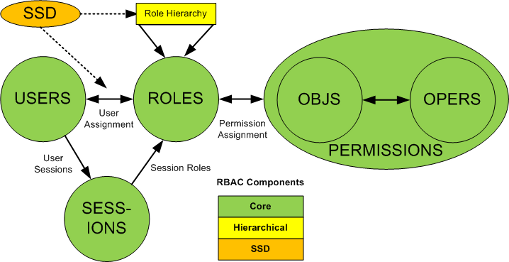
RBAC3 - Dynamic Separation of Duty (DSD) Relations
Control allowed role combinations to be activated within an RBAC session. DSD policies fine tune role policies that facilitate authorization dual control and two man policy restrictions during runtime security checks.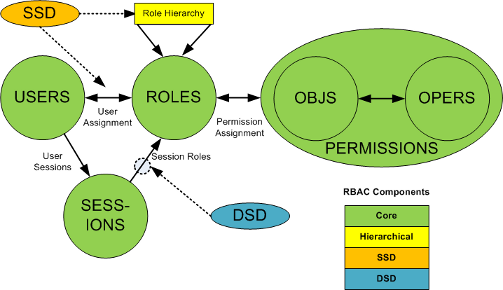
This interface's implementer will NOT be thread safe if parent instance variables (
Manageable.setContextId(String)orManageable.setAdmin(org.apache.directory.fortress.core.model.Session)) are set.- Author:
- Apache Directory Project
-
-
Method Summary
All Methods Instance Methods Abstract Methods Modifier and Type Method Description voidaddAscendant(Role childRole, Role parentRole)This command creates a new role parentRole, and inserts it in the role hierarchy as an immediate ascendant of the existing role childRole.voidaddDescendant(Role parentRole, Role childRole)This command creates a new role childRole, and inserts it in the role hierarchy as an immediate descendant of the existing role parentRole.SDSetaddDsdRoleMember(SDSet dsdSet, Role role)This command adds a role to a named DSD set of roles.voidaddInheritance(Role parentRole, Role childRole)This command establishes a new immediate inheritance relationship parentRole <<-- childRole between existing roles parentRole, childRole.PermissionaddPermission(Permission perm)This method will add permission operation to an existing permission object which resides underou=Permissions,ou=RBAC,dc=yourHostName,dc=comcontainer in directory information tree.PermissionAttributeSetaddPermissionAttributeSet(PermissionAttributeSet permAttributeSet)This method will create a new permission attribute set object with resides under theou=Constraints,ou=RBAC,dc=yourHostName,dc=comcontainer in directory information tree.PermissionAttributeaddPermissionAttributeToSet(PermissionAttribute permAttribute, String attributeSetName)This method adds a permission attribute (ftPA) to a permission attribute set.PermObjaddPermObj(PermObj pObj)This method will add permission object to perms container in directory.RoleaddRole(Role role)This command creates a new role.RoleConstraintaddRoleConstraint(UserRole uRole, RoleConstraint roleConstraint)This method adds a roleConstraint (ftRC) to the user ldap entry.SDSetaddSsdRoleMember(SDSet ssdSet, Role role)This command adds a role to a named SSD set of roles.UseraddUser(User user)This command creates a new RBAC user.voidassignUser(UserRole uRole)This command assigns a user to a role.voidchangePassword(User user, String newPassword)Method will change user's password.SDSetcreateDsdSet(SDSet dsdSet)This command creates a named DSD set of roles and sets an associated cardinality n.SDSetcreateSsdSet(SDSet ssdSet)This command creates a named SSD set of roles and sets the cardinality n of its subsets that cannot have common users.voiddeassignUser(UserRole uRole)This command deletes the assignment of the User from the Role entities.SDSetdeleteDsdRoleMember(SDSet dsdSet, Role role)This command removes a role from a named DSD set of roles.SDSetdeleteDsdSet(SDSet dsdSet)This command deletes a DSD role set completely.voiddeleteInheritance(Role parentRole, Role childRole)This command deletes an existing immediate inheritance relationship parentRole <<-- childRole.voiddeletePasswordPolicy(User user)Method will delete user's password policy designation.voiddeletePermission(Permission perm)This method will remove permission operation entity from permission object.voiddeletePermissionAttributeSet(PermissionAttributeSet permAttributeSet)This method will delete a permission attribute set object.voiddeletePermObj(PermObj pObj)This method will remove permission object to perms container in directory.voiddeleteRole(Role role)This command deletes an existing role from the RBAC database.SDSetdeleteSsdRoleMember(SDSet ssdSet, Role role)This command removes a role from a named SSD set of roles.SDSetdeleteSsdSet(SDSet ssdSet)This command deletes a SSD role set completely.voiddeleteUser(User user)This command deletes an existing user from the RBAC database.voiddisableRoleConstraint(Role role, RoleConstraint roleConstraint)This method disables a role to be constrainted by attributes.voiddisableUser(User user)This command deletes an existing user from the RBAC database.voidenableRoleConstraint(Role role, RoleConstraint roleConstraint)This method enables a role to be constrainted by attributes.voidgrantPermission(Permission perm, Role role)This command grants a role the permission to perform an operation on an object to a role.voidgrantPermission(Permission perm, User user)This command grants a user the permission to perform an operation on an object to a role.voidlockUserAccount(User user)Method will lock user's password which will prevent the user from authenticating with directory.voidremovePermissionAttributeFromSet(PermissionAttribute permAttribute, String attributeSetName)This method removed a permission attribute (ftPA) from an existing permission attribute set.voidremoveRoleConstraint(UserRole uRole, String roleConstraintId)Thie method removes a roleConstraint (ftRC) from the user ldap entry.voidremoveRoleConstraint(UserRole uRole, RoleConstraint roleConstraint)Thie method removes a roleConstraint (ftRC) from the user ldap entry.voidresetPassword(User user, String newPassword)Method will reset user's password which will require user to change password before successful authentication with directory.voidrevokePermission(Permission perm, Role role)This command revokes the permission to perform an operation on an object from the set of permissions assigned to a role.voidrevokePermission(Permission perm, User user)This command revokes the permission to perform an operation on an object from the set of permissions assigned to a user.SDSetsetDsdSetCardinality(SDSet dsdSet, int cardinality)This command sets the cardinality associated with a given DSD role set.SDSetsetSsdSetCardinality(SDSet ssdSet, int cardinality)This command sets the cardinality associated with a given SSD role set.voidunlockUserAccount(User user)Method will unlock user's password which will enable user to authenticate with directory.SDSetupdateDsdSet(SDSet dsdSet)This command updates existing DSD set of roles and sets the cardinality n of its subsets that cannot have common users.PermissionupdatePermission(Permission perm)This method will update permission operation pre-existing in target directory underou=Permissions,ou=RBAC,dc=yourHostName,dc=comcontainer in directory information tree.voidupdatePermissionAttributeInSet(PermissionAttribute permAttribute, String attributeSetName, boolean replaceValidValues)This method updates a permission attribute (ftPA) on a permission attribute set.PermObjupdatePermObj(PermObj pObj)This method will update permission object in perms container in directory.RoleupdateRole(Role role)Method will update a Role entity in the directory.SDSetupdateSsdSet(SDSet ssdSet)This command updates existing SSD set of roles and sets the cardinality n of its subsets that cannot have common users.UserupdateUser(User user)This method performs an update on User entity in directory.-
Methods inherited from interface org.apache.directory.fortress.core.Manageable
setAdmin, setContextId
-
-
-
-
Method Detail
-
addUser
User addUser(User user) throws SecurityException
This command creates a new RBAC user. The command is valid only if the new user is not already a member of the USERS data set. The USER data set is updated. The new user does not own any session at the time of its creation.required parameters
- User#userId - maps to INetOrgPerson uid
- User#password - used to authenticate the User
- User#ou - contains the name of an already existing User OU node
optional parameters
- User#pwPolicy - contains the name of an already existing OpenLDAP password policy node
- User#cn - maps to INetOrgPerson common name attribute
- User#sn - maps to INetOrgPerson surname attribute
- User#description - maps to INetOrgPerson description attribute
- User#title - maps to INetOrgPerson title attribute
- User#employeeType - maps to INetOrgPerson employeeType attribute
- User#phones * - multivalued attribute maps to organizationalPerson telephoneNumber attribute
- User#mobiles * - multivalued attribute maps to INetOrgPerson mobile attribute
- User#emails * - multivalued attribute maps to INetOrgPerson mail attribute
- User#address * - multivalued attribute maps to organizationalPerson postalAddress, st, l, postalCode, postOfficeBox attributes
- User#beginTime - HHMM - determines begin hour user may activate session
- User#endTime - HHMM - determines end hour user may activate session.
- User#beginDate - YYYYMMDD - determines date when user may sign on
- User#endDate - YYYYMMDD - indicates latest date user may sign on
- User#beginLockDate - YYYYMMDD - determines beginning of enforced inactive status
- User#endLockDate - YYYYMMDD - determines end of enforced inactive status
- User#dayMask - 1234567, 1 = Sunday, 2 = Monday, etc - specifies which day of user may sign on
- User#timeout - number (in minutes) of session inactivity time allowed
- User#props * - multivalued attribute contains property key and values are separated with a ':'. e.g. mykey1:myvalue1
- Parameters:
user- User entity must contain User#userId and User#ou (required) and optional User#description,User#roles and many others.- Returns:
- Returns entity containing user data that was added.
- Throws:
SecurityException- thrown in the event of data validation or system error.
-
disableUser
void disableUser(User user) throws SecurityException
This command deletes an existing user from the RBAC database. The command is valid if and only if the user to be deleted is a member of the USERS data set. The USERS and UA data sets and the assigned_users function are updated. Method performs a "soft" delete. It performs the following:- sets the user status to "deleted"
- deassigns all roles from the user
- locks the user's password in LDAP
- revokes all perms that have been granted to user entity.
required parameters
- User#userId - maps to INetOrgPerson uid
- Parameters:
user- Contains the User#userId of the User targeted for deletion.- Throws:
SecurityException- thrown in the event of data validation or system error.
-
deleteUser
void deleteUser(User user) throws SecurityException
This command deletes an existing user from the RBAC database. The command is valid if and only if the user to be deleted is a member of the USERS data set. The USERS and UA data sets and the assigned_users function are updated. This method performs a "hard" delete. It completely removes all data associated with this user from the directory. User entity must exist in directory prior to making this call else exception will be thrown.required parameters
- User#userId - maps to INetOrgPerson uid
- Parameters:
user- Contains the User#userId of the User targeted for deletion.- Throws:
SecurityException- thrown in the event of data validation or system error.
-
updateUser
User updateUser(User user) throws SecurityException
This method performs an update on User entity in directory. Prior to making this call the entity must exist in directory.required parameters
- User#userId - maps to INetOrgPerson uid
optional parameters
- User#password - used to authenticate the User
- User#ou - contains the name of an already existing User OU node
- User#pwPolicy - contains the name of an already existing OpenLDAP password policy node
- User#cn - maps to INetOrgPerson common name attribute
- User#sn - maps to INetOrgPerson surname attribute
- User#description - maps to INetOrgPerson description attribute
- User#title - maps to INetOrgPerson title attribute
- User#employeeType - maps to INetOrgPerson employeeType attribute
- User#phones * - multivalued attribute maps to organizationalPerson telephoneNumber attribute
- User#mobiles * - multivalued attribute maps to INetOrgPerson mobile attribute
- User#emails * - multivalued attribute maps to INetOrgPerson mail attribute
- User#address * - multivalued attribute maps to organizationalPerson postalAddress, st, l, postalCode, postOfficeBox attributes
- User#beginTime - HHMM - determines begin hour user may activate session
- User#endTime - HHMM - determines end hour user may activate session.
- User#beginDate - YYYYMMDD - determines date when user may sign on
- User#endDate - YYYYMMDD - indicates latest date user may sign on
- User#beginLockDate - YYYYMMDD - determines beginning of enforced inactive status
- User#endLockDate - YYYYMMDD - determines end of enforced inactive status
- User#dayMask - 1234567, 1 = Sunday, 2 = Monday, etc - specifies which day of user may sign on
- User#timeout - number (in minutes) of session inactivity time allowed
- User#props * - multivalued attribute contains property key and values are separated with a ':'. e.g. mykey1:myvalue1
- Parameters:
user- must contain User#userId and optional entity data to update i.e. desc, ou, properties, all attributes that are not set will be ignored.- Returns:
- Updated user entity data.
- Throws:
SecurityException- thrown in the event of validation or system error.
-
changePassword
void changePassword(User user, String newPassword) throws SecurityException
Method will change user's password. This method will evaluate user's password policies.required parameters
- User#userId - maps to INetOrgPerson uid
- User#password - contains the User's old password
- newPassword - contains the User's new password
- Parameters:
user- contains User#userId and old user password User#password.newPassword- contains new user password.- Throws:
SecurityException- will be thrown in the event of password policy violation or system error.
-
lockUserAccount
void lockUserAccount(User user) throws SecurityException
Method will lock user's password which will prevent the user from authenticating with directory.required parameters
- User#userId - maps to INetOrgPerson uid
- Parameters:
user- entity contains User#userId of User to be locked.- Throws:
SecurityException- will be thrown in the event of pw policy violation or system error.
-
unlockUserAccount
void unlockUserAccount(User user) throws SecurityException
Method will unlock user's password which will enable user to authenticate with directory.required parameters
- User#userId - maps to INetOrgPerson uid
- Parameters:
user- entity contains User#userId of User to be unlocked.- Throws:
SecurityException- will be thrown in the event of pw policy violation or system error.
-
resetPassword
void resetPassword(User user, String newPassword) throws SecurityException
Method will reset user's password which will require user to change password before successful authentication with directory. This method will not evaluate password policies on the new user password as it must be changed before use.required parameters
- User#userId - maps to INetOrgPerson uid
- newPassword - contains the User's new password
- Parameters:
user- entity contains User#userId of User to be reset.newPassword- The new password to set- Throws:
SecurityException- will be thrown in the event of pw policy violation or system error.
-
deletePasswordPolicy
void deletePasswordPolicy(User user) throws SecurityException
Method will delete user's password policy designation.required parameters
- User#userId - maps to INetOrgPerson uid
- newPassword - contains the User's new password
- Parameters:
user- contains User#userId.- Throws:
SecurityException- will be thrown in the event of password policy violation or system error.
-
addRole
Role addRole(Role role) throws SecurityException
This command creates a new role. The command is valid if and only if the new role is not already a member of the ROLES data set. The ROLES data set is updated. Initially, no user or permission is assigned to the new role.required parameters
- Role#name - contains the name to use for the Role to be created.
optional parameters
- Role#description - maps to description attribute on organizationalRole object class
- Role#beginTime - HHMM - determines begin hour role may be activated into user's RBAC session
- Role#endTime - HHMM - determines end hour role may be activated into user's RBAC session.
- Role#beginDate - YYYYMMDD - determines date when role may be activated into user's RBAC session
- Role#endDate - YYYYMMDD - indicates latest date role may be activated into user's RBAC session
- Role#beginLockDate - YYYYMMDD - determines beginning of enforced inactive status
- Role#endLockDate - YYYYMMDD - determines end of enforced inactive status
- Role#dayMask - 1234567, 1 = Sunday, 2 = Monday, etc - specifies which day role may be activated into user's RBAC session
- Parameters:
role- must contains Role#name (required) and optional Role#description.- Returns:
- copy of the added Role
- Throws:
SecurityException- thrown in the event of data validation or system error.
-
deleteRole
void deleteRole(Role role) throws SecurityException
This command deletes an existing role from the RBAC database. The command is valid if and only if the role to be deleted is a member of the ROLES data set. This command will also deassign role from all users.required parameters
- Role#name - contains the name to use for the Role to be deleted.
- Parameters:
role- Must contain Role#name for Role to delete.- Throws:
SecurityException- thrown in the event of data validation or system error.
-
updateRole
Role updateRole(Role role) throws SecurityException
Method will update a Role entity in the directory. The role must exist in role container prior to this call.required parameters
- Role#name - contains the name to use for the Role to be updated.
optional parameters
- Role#description - maps to description attribute on organizationalRole object class
- Role#beginTime - HHMM - determines begin hour role may be activated into user's RBAC session
- Role#endTime - HHMM - determines end hour role may be activated into user's RBAC session.
- Role#beginDate - YYYYMMDD - determines date when role may be activated into user's RBAC session
- Role#endDate - YYYYMMDD - indicates latest date role may be activated into user's RBAC session
- Role#beginLockDate - YYYYMMDD - determines beginning of enforced inactive status
- Role#endLockDate - YYYYMMDD - determines end of enforced inactive status
- {Role#dayMask - 1234567, 1 = Sunday, 2 = Monday, etc - specifies which day role may be activated into user's RBAC session
- Parameters:
role- Must contains Role#name and may contain new description orConstraint- Returns:
- Role contains reference to entity operated on.
- Throws:
SecurityException- in the event of validation or system error.
-
assignUser
void assignUser(UserRole uRole) throws SecurityException
This command assigns a user to a role.- The command is valid if and only if:
-
- The user is a member of the USERS data set
- The role is a member of the ROLES data set
- The user is not already assigned to the role
- The SSD constraints are satisfied after assignment.
Successful completion of this op, the following occurs:
- User entity (resides in people container) has role assignment added to aux object class attached to actual user record.
- Role entity (resides in role container) has userId added as role occupant.
- (optional) Temporal constraints may be associated with
ftUserAttrsaux object class based on: -
- timeout - number (in minutes) of session inactivity time allowed.
- beginDate - YYYYMMDD - determines date when role may be activated.
- endDate - YYMMDD - indicates latest date role may be activated.
- beginLockDate - YYYYMMDD - determines beginning of enforced inactive status
- endLockDate - YYMMDD - determines end of enforced inactive status.
- beginTime - HHMM - determines begin hour role may be activated in user's session.
- endTime - HHMM - determines end hour role may be activated in user's session.*
- dayMask - 1234567, 1 = Sunday, 2 = Monday, etc - specifies which day of week role may be activated.
required parameters
- UserRole#name - contains the name for already existing Role to be assigned
- UserRole#userId - contains the userId for existing User
optional parameters
- UserRole#beginTime - HHMM - determines begin hour role may be activated into user's RBAC session
- UserRole#endTime - HHMM - determines end hour role may be activated into user's RBAC session.
- UserRole#beginDate - YYYYMMDD - determines date when role may be activated into user's RBAC session
- UserRole#endDate - YYYYMMDD - indicates latest date role may be activated into user's RBAC session
- UserRole#beginLockDate - YYYYMMDD - determines beginning of enforced inactive status
- UserRole#endLockDate - YYYYMMDD - determines end of enforced inactive status
- UserRole#dayMask - 1234567, 1 = Sunday, 2 = Monday, etc - specifies which day role may be activated into user's RBAC session
- Parameters:
uRole- must contain UserRole#userId and UserRole#name and optionalConstraints.- Throws:
SecurityException- in the event of validation or system error.
-
enableRoleConstraint
void enableRoleConstraint(Role role, RoleConstraint roleConstraint) throws SecurityException
This method enables a role to be constrainted by attributes.required parameters
- Role#name - contains the name for already existing Role to be constrained
- RoleConstraint#key - contains the name of the constraint, e.g. locale, organization, or accountnumber
- Parameters:
role- must contain Role#nameroleConstraint- must contain RoleConstraint#key- Throws:
SecurityException- in the event of validation or system error.
-
disableRoleConstraint
void disableRoleConstraint(Role role, RoleConstraint roleConstraint) throws SecurityException
This method disables a role to be constrainted by attributes.required parameters
- Role#name - contains the name for already existing Role to be unconstrained
- RoleConstraint#key - contains the name of the constraint, e.g. locale, organization, or accountnumber
- Parameters:
role- must contain Role#nameroleConstraint- must contain RoleConstraint#key- Throws:
SecurityException- in the event of validation or system error.
-
addRoleConstraint
RoleConstraint addRoleConstraint(UserRole uRole, RoleConstraint roleConstraint) throws SecurityException
This method adds a roleConstraint (ftRC) to the user ldap entry. (ftRC=ROLE_NAME$type$CONSTRAINT_TYPE$CONSTRAINT_PASETNAME$CONSTRAINT_VALUE)required parameters
- UserRole#name - contains the name for already existing Role to be assigned
- UserRole#userId - contains the userId for existing User
- RoleConstraint#type - contains the type of role constraint (filter, other)
- RoleConstraint#value - contains the value of the role constraint which is currently not validated in any way
- RoleConstraint#key - contains the name of the permission attribute set this constraint is applicable for
- Parameters:
uRole- must contain UserRole#userId and UserRole#nameroleConstraint- must contain RoleConstraint#type, RoleConstraint#value and RoleConstraint#paSetName- Returns:
- RoleConstraint that was added to user role assignment
- Throws:
SecurityException- in the event of validation or system error.
-
removeRoleConstraint
void removeRoleConstraint(UserRole uRole, RoleConstraint roleConstraint) throws SecurityException
Thie method removes a roleConstraint (ftRC) from the user ldap entry.required parameters
- UserRole#name - contains the name for already existing Role to be assigned
- UserRole#userId - contains the userId for existing User
- RoleConstraint#type - contains the type of role constraint (filter, other)
- RoleConstraint#value - contains the value of the role constraint which is currently not validated in any way
- RoleConstraint#paSetName - contains the name of the permission attribute set this constraint is applicable for
- Parameters:
uRole- must contain UserRole#userId and UserRole#nameroleConstraint- must contain RoleConstraint#type, RoleConstraint#value and RoleConstraint#paSetName- Throws:
SecurityException- in the event of validation or system error.
-
removeRoleConstraint
void removeRoleConstraint(UserRole uRole, String roleConstraintId) throws SecurityException
Thie method removes a roleConstraint (ftRC) from the user ldap entry.required parameters
- UserRole#name - contains the name for already existing Role to be assigned
- UserRole#userId - contains the userId for existing User
- RoleConstraint#type - contains the type of role constraint (filter, other)
- RoleConstraint#value - contains the value of the role constraint which is currently not validated in any way
- RoleConstraint#paSetName - contains the userId for existing User, contains the name of the permission attribute set this constraint is applicable for
- Parameters:
uRole- must contain UserRole#userId} and UserRole#name}roleConstraintId- id of the role constraint to remove- Throws:
SecurityException- in the event of validation or system error.
-
deassignUser
void deassignUser(UserRole uRole) throws SecurityException
This command deletes the assignment of the User from the Role entities. The command is valid if and only if the user is a member of the USERS data set, the role is a member of the ROLES data set, and the user is assigned to the role. Any sessions that currently have this role activated will not be effected. Successful completion includes:- User entity in USER data set has role assignment removed.
- Role entity in ROLE data set has userId removed as role occupant.
- (optional) Temporal constraints will be removed from user aux object if set prior to call.
required parameters
- UserRole#name - contains the name for already existing Role to be deassigned
- UserRole#userId - contains the userId for existing User
- Parameters:
uRole- must contain org.apache.directory.fortress.core.model.UserRole#userId} and UserRole#name}.- Throws:
SecurityException- - in the event data error in user or role objects or system error.
-
addPermission
Permission addPermission(Permission perm) throws SecurityException
This method will add permission operation to an existing permission object which resides underou=Permissions,ou=RBAC,dc=yourHostName,dc=comcontainer in directory information tree. The perm operation entity may haveRoleorUserassociations. The target Permission} must not exist prior to calling. A Fortress Permission instance exists in a hierarchical, one-many relationship between its parent and itself as stored in ldap tree: (PermObj*->Permission).required parameters
- Permission#objName - contains the name of existing object being targeted for the permission add
- Permission#opName - contains the name of new permission operation being added
optional parameters
- Permission#roles} * - multi occurring attribute contains RBAC Roles that permission operation is being granted to
- Permission#users} * - multi occurring attribute contains Users that permission operation is being granted to
- Permission#props} * - multi-occurring property key and values are separated with a ':'. e.g. mykey1:myvalue1
- Permission#type - any safe text
- Parameters:
perm- must contain the object, org.apache.directory.fortress.core.model.Permission#objName}, and operation, Permission#opName}, that identifies target along with optional other attributes..- Returns:
- copy of Permission entity.
- Throws:
SecurityException- - thrown in the event of perm object data or system error.
-
addPermissionAttributeSet
PermissionAttributeSet addPermissionAttributeSet(PermissionAttributeSet permAttributeSet) throws SecurityException
This method will create a new permission attribute set object with resides under theou=Constraints,ou=RBAC,dc=yourHostName,dc=comcontainer in directory information tree. The attribute set may contain 0 to manyPermissionAttributerequired parameters
- PermissionAttributeSet#name - contains the name of the permission attribute set
- Parameters:
permAttributeSet- must contain PermissionAttributeSet#name}- Returns:
- PermissionAttributeSet that was created
- Throws:
SecurityException- - thrown in the event of perm attribute set data or system error.
-
deletePermissionAttributeSet
void deletePermissionAttributeSet(PermissionAttributeSet permAttributeSet) throws SecurityException
This method will delete a permission attribute set object.required parameters
- PermissionAttributeSet#name - contains the name of the permission attribute set
- Parameters:
permAttributeSet- must contain PermissionAttributeSet#name}- Throws:
SecurityException- - thrown in the event of perm attribute set data or system error.
-
addPermissionAttributeToSet
PermissionAttribute addPermissionAttributeToSet(PermissionAttribute permAttribute, String attributeSetName) throws SecurityException
This method adds a permission attribute (ftPA) to a permission attribute set.required parameters
- PermissionAttribute#attributeName - contains the name of existing object being targeted for the permission update
- PermissionAttribute#dataType - contains the data type of the permission attribute values (string,int,long,float)
- attributeSetName - contains the name of existing permission attribute set being modified
optional parameters
- PermissionAttribute#required - Flag to specify this attribute is required, defaults to false.
- PermissionAttribute#operator - Can specify an operator this attribute must use.
- PermissionAttribute#validValues - CSV of valid values. Currently up to interpreting application to understand these.
- PermissionAttribute#defaultValue - A default value for the attribute value if none is specified.
- Parameters:
permAttribute- must contain PermissionAttribute#attributeName} and PermissionAttribute#dataType}attributeSetName- The name of the permission attribute set this ftPA should be added.- Returns:
- PermissionAttribute entity created
- Throws:
SecurityException- - thrown in the event of data or system error
-
removePermissionAttributeFromSet
void removePermissionAttributeFromSet(PermissionAttribute permAttribute, String attributeSetName) throws SecurityException
This method removed a permission attribute (ftPA) from an existing permission attribute set.required parameters
- PermissionAttribute#attributeName - contains the name of existing object being targeted for the permission update
- attributeSetName - contains the name of existing permission attribute set being modified
- Parameters:
permAttribute- must contain PermissionAttribute#attributeName}attributeSetName- The name of the permission attribute set this pa should be removed from- Throws:
SecurityException- - thrown in the event of data or system error
-
updatePermissionAttributeInSet
void updatePermissionAttributeInSet(PermissionAttribute permAttribute, String attributeSetName, boolean replaceValidValues) throws SecurityException
This method updates a permission attribute (ftPA) on a permission attribute set.required parameters
- PermissionAttribute#attributeName - contains the name of existing object being targeted for the permission update
- PermissionAttribute#dataType - contains the data type of the permission attribute values (string,int,long,float)
- attributeSetName - contains the name of existing permission attribute set being modified
optional parameters
- PermissionAttribute#required - Flag to specify this attribute is required, defaults to false.
- PermissionAttribute#operator - Can specify an operator this attribute must use.
- PermissionAttribute#validValues - CSV of valid values. Currently up to interpreting application to understand these.
- PermissionAttribute#defaultValue - A default value for the attribute value if none is specified.
- Parameters:
permAttribute- must contain PermissionAttribute#attributeName} and PermissionAttribute#dataType}attributeSetName- The name of the permission attribute set this ftPA should be updated.- Throws:
SecurityException- - thrown in the event of data or system error
-
updatePermission
Permission updatePermission(Permission perm) throws SecurityException
This method will update permission operation pre-existing in target directory underou=Permissions,ou=RBAC,dc=yourHostName,dc=comcontainer in directory information tree. The perm operation entity may also containRoleorUserassociations to add or remove using this function. The perm operation must exist before making this call. Only non-null attributes will be updated.required parameters
- Permission#objName - contains the name of existing object being targeted for the permission update
- Permission#opName - contains the name of existing permission operation being updated
optional parameters
- Permission#roles} * - multi occurring attribute contains RBAC Roles that permission operation is being granted to
- Permission#users} * - multi occurring attribute contains Users that permission operation is being granted to
- Permission#props} * - multi-occurring property key and values are separated with a ':'. e.g. mykey1:myvalue1
- Permission#type - any safe text
- Parameters:
perm- must contain the object, Permission#objName}, and operation, Permission#opName}, that identifies target and any optional data to update. Null or empty attributes will be ignored.- Returns:
- copy of Permission entity.
- Throws:
SecurityException- - thrown in the event of perm object data or system error.
-
deletePermission
void deletePermission(Permission perm) throws SecurityException
This method will remove permission operation entity from permission object. A Fortress permission is (object->operation). The perm operation must exist before making this call.required parameters
- Permission#objName - contains the name of existing object being targeted for the permission delete
- Permission#opName - contains the name of existing permission operation being removed
- Parameters:
perm- must contain the object, Permission#objName}, and operation, Permission#opName}, that identifies target.- Throws:
SecurityException- - thrown in the event of perm object data or system error.
-
addPermObj
PermObj addPermObj(PermObj pObj) throws SecurityException
This method will add permission object to perms container in directory. The perm object must not exist before making this call. APermObjinstance exists in a hierarchical, one-many relationship between itself and children as stored in ldap tree: (PermObj*->Permission}).required parameters
- PermObj#objName - contains the name of new object being added
- PermObj#ou - contains the name of an existing PERMS OrgUnit this object is associated with
optional parameters
- PermObj#description - any safe text
- PermObj#type - contains any safe text
- PermObj#props} * - multi-occurring property key and values are separated with a ':'. e.g. mykey1:myvalue1
- Parameters:
pObj- must contain the PermObj#objName} and PermObj#ou}. The other attributes are optional.- Returns:
- copy of PermObj entity.
- Throws:
SecurityException- - thrown in the event of perm object data or system error.
-
updatePermObj
PermObj updatePermObj(PermObj pObj) throws SecurityException
This method will update permission object in perms container in directory. The perm object must exist before making this call. APermObjinstance exists in a hierarchical, one-many relationship between itself and children as stored in ldap tree: (PermObj*->Permission).required parameters
- PermObj#objName - contains the name of existing object being updated
optional parameters
- PermObj#ou - contains the name of an existing PERMS OrgUnit this object is associated with
- PermObj#description - any safe text
- PermObj#type - contains any safe text
- PermObj#props} * - multi-occurring property key and values are separated with a ':'. e.g. mykey1:myvalue1
- Parameters:
pObj- must contain the PermObj#objName}. Only non-null attributes will be updated.- Returns:
- copy of newly updated PermObj entity.
- Throws:
SecurityException- - thrown in the event of perm object data or system error.
-
deletePermObj
void deletePermObj(PermObj pObj) throws SecurityException
This method will remove permission object to perms container in directory. This method will also remove in associated permission objects that are attached to this object.required parameters
- PermObj#objName - contains the name of existing object targeted for removal
- Parameters:
pObj- must contain the PermObj#objName} of object targeted for removal.- Throws:
SecurityException- - thrown in the event of perm object data or system error.
-
grantPermission
void grantPermission(Permission perm, Role role) throws SecurityException
This command grants a role the permission to perform an operation on an object to a role. The command is implemented by granting permission by setting the access control list of the object involved. The command is valid if and only if the pair (operation, object) represents a permission, and the role is a member of the ROLES data set.required parameters
- Permission#objName - contains the object name
- Permission#opName - contains the operation name
- Role#name - contains the role name
- Parameters:
perm- must contain the object, Permission#objName}, and operation, Permission#opName}, that identifies target.role- must contains Role#name}.- Throws:
SecurityException- Thrown in the event of data validation or system error.
-
revokePermission
void revokePermission(Permission perm, Role role) throws SecurityException
This command revokes the permission to perform an operation on an object from the set of permissions assigned to a role. The command is implemented by setting the access control list of the object involved. The command is valid if and only if the pair (operation, object) represents a permission, the role is a member of the ROLES data set, and the permission is assigned to that role.required parameters
- Permission#objName - contains the object name
- Permission#opName - contains the operation name
- Role#name - contains the role name
- Parameters:
perm- must contain the object, Permission#objName}, and operation, Permission#opName}, that identifies target.role- must contains Role#name}.- Throws:
SecurityException- Thrown in the event of data validation or system error.
-
grantPermission
void grantPermission(Permission perm, User user) throws SecurityException
This command grants a user the permission to perform an operation on an object to a role. The command is implemented by granting permission by setting the access control list of the object involved. The command is valid if and only if the pair (operation, object) represents a permission, and the user is a member of the USERS data set.required parameters
- Permission#objName - contains the object name
- Permission#opName - contains the operation name
- User#userId - contains the userId
- Parameters:
perm- must contain the object, Permission#objName}, and operation, Permission#opName}, that identifies target.user- must contain User#userId} of target User entity.- Throws:
SecurityException- Thrown in the event of data validation or system error.
-
revokePermission
void revokePermission(Permission perm, User user) throws SecurityException
This command revokes the permission to perform an operation on an object from the set of permissions assigned to a user. The command is implemented by setting the access control list of the object involved. The command is valid if and only if the pair (operation, object) represents a permission, the user is a member of the USERS data set, and the permission is assigned to that user.required parameters
- Permission#objName - contains the object name
- Permission#opName - contains the operation name
- User#userId - contains the userId
- Parameters:
perm- must contain the object, Permission#objName}, and operation, Permission#opName}, that identifies target.user- must contain User#userId} of target User entity.- Throws:
SecurityException- Thrown in the event of data validation or system error.
-
addDescendant
void addDescendant(Role parentRole, Role childRole) throws SecurityException
This command creates a new role childRole, and inserts it in the role hierarchy as an immediate descendant of the existing role parentRole.The command is valid if and only if:
- The childRole is not a member of the ROLES data set.
- The parentRole is a member of the ROLES data set.
This method:
- Adds new role.
- Assigns role relationship between new childRole and pre-existing parentRole.
required parameters
- parentRole - Role#name - contains the name of existing Role to be parent
- childRole - Role#name - contains the name of new Role to be child
optional parameters childRole
- childRole - Role#description - maps to description attribute on organizationalRole object class for new child
- childRole - Role#beginTime - HHMM - determines begin hour role may be activated into user's RBAC session for new child
- childRole - Role#endTime - HHMM - determines end hour role may be activated into user's RBAC session for new child
- childRole - Role#beginDate - YYYYMMDD - determines date when role may be activated into user's RBAC session for new child
- childRole - Role#endDate - YYYYMMDD - indicates latest date role may be activated into user's RBAC session for new child
- childRole - Role#beginLockDate - YYYYMMDD - determines beginning of enforced inactive status for new child
- childRole - Role#endLockDate - YYYYMMDD - determines end of enforced inactive status for new child
- childRole - Role#dayMask - 1234567, 1 = Sunday, 2 = Monday, etc - specifies which day role may be activated into user's RBAC session for new child
- Parameters:
parentRole- This entity must be present in ROLE data set. Success will add role rel with childRole.childRole- This entity must not be present in ROLE data set. Success will add the new role entity to ROLE data set.- Throws:
SecurityException- thrown in the event of data validation or system error.
-
addAscendant
void addAscendant(Role childRole, Role parentRole) throws SecurityException
This command creates a new role parentRole, and inserts it in the role hierarchy as an immediate ascendant of the existing role childRole.The command is valid if and only if:
- The parentRole is not a member of the ROLES data set.
- The childRole is a member of the ROLES data set.
This method:
- Adds new role.
- Assigns role relationship between new parentRole and pre-existing childRole.
required parameters
- childRole - Role#name - contains the name of existing child Role
- parentRole - Role#name - contains the name of new Role to be parent
optional parameters parentRole
- parentRole - Role#description - maps to description attribute on organizationalRole object class for new parent
- parentRole - Role#beginTime - HHMM - determines begin hour role may be activated into user's RBAC session for new parent
- parentRole - Role#endTime - HHMM - determines end hour role may be activated into user's RBAC session for new parent
- parentRole - Role#beginDate - YYYYMMDD - determines date when role may be activated into user's RBAC session for new parent
- parentRole - Role#endDate - YYYYMMDD - indicates latest date role may be activated into user's RBAC session for new parent
- parentRole - Role#beginLockDate - YYYYMMDD - determines beginning of enforced inactive status for new parent
- parentRole - Role#endLockDate - YYYYMMDD - determines end of enforced inactive status for new parent
- parentRole - Role#dayMask - 1234567, 1 = Sunday, 2 = Monday, etc - specifies which day role may be activated into user's RBAC session for new parent
- Parameters:
parentRole- completion of op assigns new child relationship with childRole.childRole- completion of op assigns new parent relationship with parentRole.- Throws:
SecurityException- thrown in the event of data validation or system error.
-
addInheritance
void addInheritance(Role parentRole, Role childRole) throws SecurityException
This command establishes a new immediate inheritance relationship parentRole <<-- childRole between existing roles parentRole, childRole.The command is valid if and only if:
- The parentRole and childRole are members of the ROLES data set.
- The parentRole is not an immediate ascendant of childRole.
- The childRole does not properly inherit parentRole (in order to avoid cycle creation).
required parameters
- parentRole - Role#name - contains the name of existing Role to be parent
- childRole - Role#name - contains the name of existing Role to be child
- Parameters:
parentRole- completion of op deassigns child relationship with childRole.childRole- completion of op deassigns parent relationship with parentRole.- Throws:
SecurityException- thrown in the event of data validation or system error.
-
deleteInheritance
void deleteInheritance(Role parentRole, Role childRole) throws SecurityException
This command deletes an existing immediate inheritance relationship parentRole <<-- childRole.The command is valid if and only if:
- The roles parentRole and childRole are members of the ROLES data set.
- The parentRole is an immediate ascendant of childRole.
- The new inheritance relation is computed as the reflexive-transitive closure of the immediate inheritance relation resulted after deleting the relationship parentRole <<-- childRole.
required parameters
- parentRole - Role#name - contains the name of existing Role to remove parent relationship
- childRole - Role#name - contains the name of existing Role to remove child relationship
- Parameters:
parentRole- completion of op removes child relationship with childRole.childRole- completion of op removes parent relationship with parentRole.- Throws:
SecurityException- thrown in the event of data validation or system error.
-
createSsdSet
SDSet createSsdSet(SDSet ssdSet) throws SecurityException
This command creates a named SSD set of roles and sets the cardinality n of its subsets that cannot have common users.The command is valid if and only if:
- The name of the SSD set is not already in use.
- All the roles in the SSD set are members of the ROLES data set.
- n is a natural number greater than or equal to 2 and less than or equal to the cardinality of the SSD role set.
- The SSD constraint for the new role set is satisfied.
required parameters
- SDSet#name - contains the name of new SSD role set to be added
optional parameters
- SDSet#members} * - multivalued attribute contains the RBAC Role names to be added to this set
- SDSet#cardinality - default is 2 which is one more than maximum number of Roles that may be assigned to User from a particular set
- SDSet#description - contains any safe text
- Parameters:
ssdSet- contains an instantiated reference to new SSD set containing, name, members, and cardinality (default 2)- Returns:
- reference to newly created SSDSet object.
- Throws:
SecurityException- in the event of data validation or system error.
-
updateSsdSet
SDSet updateSsdSet(SDSet ssdSet) throws SecurityException
This command updates existing SSD set of roles and sets the cardinality n of its subsets that cannot have common users.The command is valid if and only if:
- The name of the SSD set already exists.
- All the roles in the SSD set are members of the ROLES data set.
- n is a natural number greater than or equal to 2 and less than or equal to the cardinality of the SSD role set.
- The SSD constraint for the new role set is satisfied.
required parameters
- SDSet#name - contains the name of existing SSD role set to be updated
optional parameters
- SDSet#members} * - multivalued attribute contains the RBAC Role names to be added to this set
- SDSet#cardinality - default is 2 which is one more than maximum number of Roles that may be assigned to User from a particular set
- SDSet#description - contains any safe text
- Parameters:
ssdSet- contains an instantiated reference to existing SSD set containing, name, members, and cardinality (default 2)- Returns:
- reference to SSDSet object targeted for update.
- Throws:
SecurityException- in the event of data validation or system error.
-
addSsdRoleMember
SDSet addSsdRoleMember(SDSet ssdSet, Role role) throws SecurityException
This command adds a role to a named SSD set of roles. The cardinality associated with the role set remains unchanged.The command is valid if and only if:
- The SSD role set exists.
- The role to be added is a member of the ROLES data set but not of a member of the SSD role set.
- The SSD constraint is satisfied after the addition of the role to the SSD role set.
required parameters
- SDSet#name - contains the name of SSD role set to be modified
- Role#name - contains the name of new SDSet#members} to be added
- Parameters:
ssdSet- contains an instantiated reference to new SSD set containing, namerole- contains instantiated Role object with role name field set.- Returns:
- reference to updated SSDSet object.
- Throws:
SecurityException- in the event of data validation or system error.
-
deleteSsdRoleMember
SDSet deleteSsdRoleMember(SDSet ssdSet, Role role) throws SecurityException
This command removes a role from a named SSD set of roles. The cardinality associated with the role set remains unchanged.The command is valid if and only if:
- The SSD role set exists.
- The role to be removed is a member of the SSD role set.
- The cardinality associated with the SSD role set is less than the number of elements of the SSD role set.
required parameters
- SDSet#name - contains the name of SSD role set to be modified
- Role#name - contains the name of existing SDSet#members} to be removed
- Parameters:
ssdSet- contains an instantiated reference to new SSD set containing name.role- contains instantiated Role object with role name field set.- Returns:
- reference to updated SSDSet object.
- Throws:
SecurityException- in the event of data validation or system error.
-
deleteSsdSet
SDSet deleteSsdSet(SDSet ssdSet) throws SecurityException
This command deletes a SSD role set completely. The command is valid if and only if the SSD role set exists.required parameters
- SDSet#name - contains the name of SSD role set to be removed
- Parameters:
ssdSet- contains an instantiated reference to SSD set targeted for removal.- Returns:
- reference to deleted SSDSet object.
- Throws:
SecurityException- in the event of data validation or system error.
-
setSsdSetCardinality
SDSet setSsdSetCardinality(SDSet ssdSet, int cardinality) throws SecurityException
This command sets the cardinality associated with a given SSD role set.The command is valid if and only if:
- The SSD role set exists.
- The new cardinality is a natural number greater than or equal to 2 and less than or equal to the number of elements of the SSD role set.
- The SSD constraint is satisfied after setting the new cardinality.
required parameters
- SDSet#name - contains the name of SSD role set to be modified
- cardinality - contains new cardinality setting for SSD
- Parameters:
ssdSet- contains an instantiated reference to new SSD set containing, namecardinality- integer value contains new cardinality value for data set.- Returns:
- reference to updated SSDSet object.
- Throws:
SecurityException- in the event of data validation or system error.
-
createDsdSet
SDSet createDsdSet(SDSet dsdSet) throws SecurityException
This command creates a named DSD set of roles and sets an associated cardinality n. The DSD constraint stipulates that the DSD role set cannot contain n or more roles simultaneously active in the same session.The command is valid if and only if:
- The name of the DSD set is not already in use.
- All the roles in the DSD set are members of the ROLES data set.
- n is a natural number greater than or equal to 2 and less than or equal to the cardinality of the DSD role set.
- The DSD constraint for the new role set is satisfied.
required parameters
- SDSet#name - contains the name of new DSD role set to be added
optional parameters
- SDSet#members} * - multivalued attribute contains the RBAC Role names to be added to this set
- SDSet#cardinality - default is 2 which is one more than maximum number of Roles that may be assigned to User from a particular set
- SDSet#description - contains any safe text
- Parameters:
dsdSet- contains an instantiated reference to new DSD set containing, name, members, and cardinality (default 2)- Returns:
- reference to newly created SSDSet object.
- Throws:
SecurityException- in the event of data validation or system error.
-
updateDsdSet
SDSet updateDsdSet(SDSet dsdSet) throws SecurityException
This command updates existing DSD set of roles and sets the cardinality n of its subsets that cannot have common users.The command is valid if and only if:
- The name of the DSD set already exists.
- All the roles in the DSD set are members of the ROLES data set.
- n is a natural number greater than or equal to 2 and less than or equal to the cardinality of the DSD role set.
- The DSD constraint for the new role set is satisfied.
required parameters
- SDSet#name - contains the name of existing DSD role set to be updated
optional parameters
- SDSet#members} * - multivalued attribute contains the RBAC Role names to be added to this set
- SDSet#cardinality - default is 2 which is one more than maximum number of Roles that may be assigned to User from a particular set
- SDSet#description - contains any safe text
- Parameters:
dsdSet- contains an instantiated reference to existing DSD set containing, name, members, and cardinality (default 2)- Returns:
- reference to DSDSet object targeted for update.
- Throws:
SecurityException- in the event of data validation or system error.
-
addDsdRoleMember
SDSet addDsdRoleMember(SDSet dsdSet, Role role) throws SecurityException
This command adds a role to a named DSD set of roles. The cardinality associated with the role set remains unchanged.The command is valid if and only if:
- The DSD role set exists.
- The role to be added is a member of the ROLES data set but not of a member of the DSD role set.
- The DSD constraint is satisfied after the addition of the role to the SSD role set.
required parameters
- SDSet#name - contains the name of DSD role set to be modified
- Role#name - contains the name of new SDSet#members} to be added
- Parameters:
dsdSet- contains an instantiated reference to new DSD set containing, namerole- contains instantiated Role object with role name field set.- Returns:
- reference to updated DSDSet object.
- Throws:
SecurityException- in the event of data validation or system error.
-
deleteDsdRoleMember
SDSet deleteDsdRoleMember(SDSet dsdSet, Role role) throws SecurityException
This command removes a role from a named DSD set of roles. The cardinality associated with the role set remains unchanged.The command is valid if and only if:
- The DSD role set exists
- The role to be removed is a member of the DSD role set.
- The cardinality associated with the DSD role set is less than the number of elements of the DSD role set.
required parameters
- SDSet#name - contains the name of DSD role set to be modified
- Role#name - contains the name of existing SDSet#members} to be removed
- Parameters:
dsdSet- contains an instantiated reference to new DSD set containing name.role- contains instantiated Role object with role name field set.- Returns:
- reference to updated DSDSet object.
- Throws:
SecurityException- in the event of data validation or system error.
-
deleteDsdSet
SDSet deleteDsdSet(SDSet dsdSet) throws SecurityException
This command deletes a DSD role set completely. The command is valid if and only if the DSD role set exists.required parameters
- SDSet#name - contains the name of DSD role set to be removed
- Parameters:
dsdSet- contains an instantiated reference to DSD set targeted for removal.- Returns:
- reference to deleted DSDSet object.
- Throws:
SecurityException- in the event of data validation or system error.
-
setDsdSetCardinality
SDSet setDsdSetCardinality(SDSet dsdSet, int cardinality) throws SecurityException
This command sets the cardinality associated with a given DSD role set.The command is valid if and only if:
- The SSD role set exists.
- The new cardinality is a natural number greater than or equal to 2 and less than or equal to the number of elements of the SSD role set.
- The SSD constraint is satisfied after setting the new cardinality.
required parameters
- SDSet#name - contains the name of DSD role set to be modified
- cardinality - contains new cardinality setting for SSD
- Parameters:
dsdSet- contains an instantiated reference to new DSD set containing, namecardinality- integer value contains new cardinality value for data set.- Returns:
- reference to updated DSDSet object.
- Throws:
SecurityException- in the event of data validation or system error.
-
-